SAML single sign-on
SAML single sign-on (SSO) gives users access to Crowdin Enterprise through an identity provider (IDP) of your choice. The benefits of SAML authentication include:
- Standardization: SAML is a standard format that allows seamless interoperability between systems, independent of implementation.
- Improved user experience: Users can access Crowdin Enterprise using your organization’s identity provider without additional authentication, allowing them to use only one set of login details.
- Increased security: SAML is a security standard for logging into applications, which provides a single point of authentication, keeping user credentials within the firewall boundary.
To get started, you’ll need to set up a connection (or connector) for Crowdin Enterprise with your IDP (for example, Auth0, Google Workspace (SAML), Okta, and others).
Once you configured your identity provider, an Organization admin can enable the SAML SSO feature in Crowdin Enterprise Organization Settings.
- Click on your profile picture in the upper-right corner and select Organization Settings.
- Switch to the Authentication section on the left sidebar and click on the SAML authentication method at the bottom of the page.
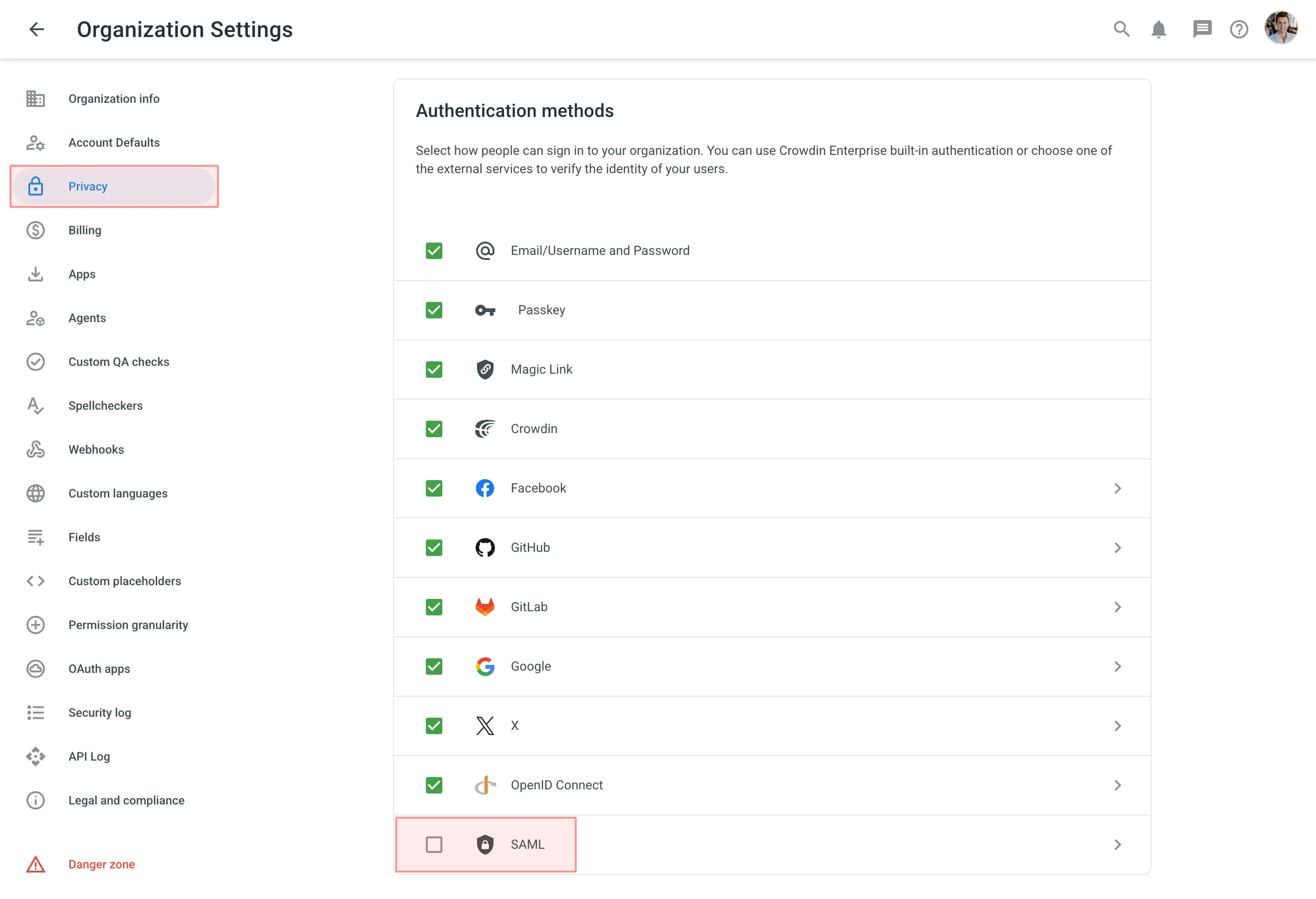
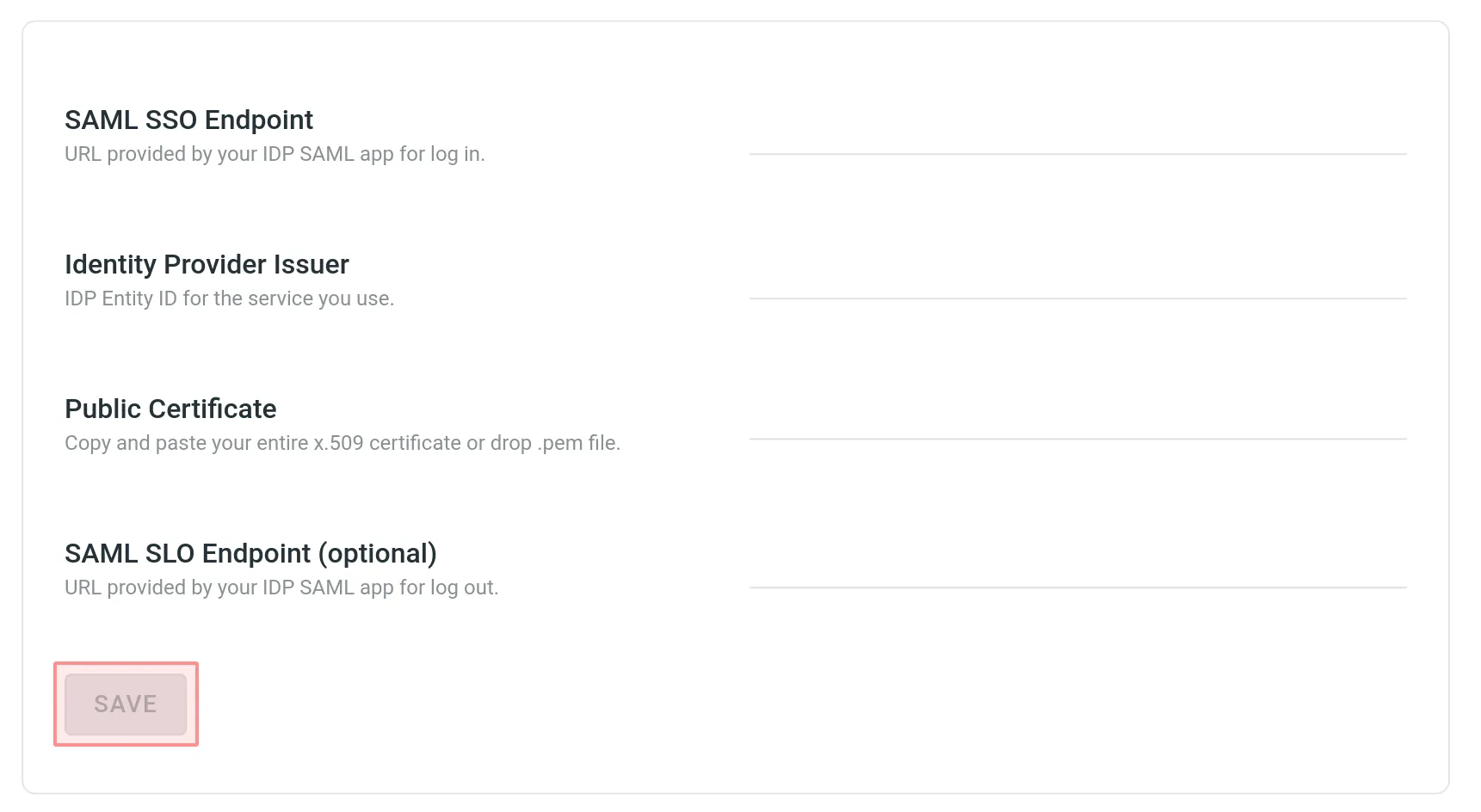
- Paste your credentials from your IDP and click Save.
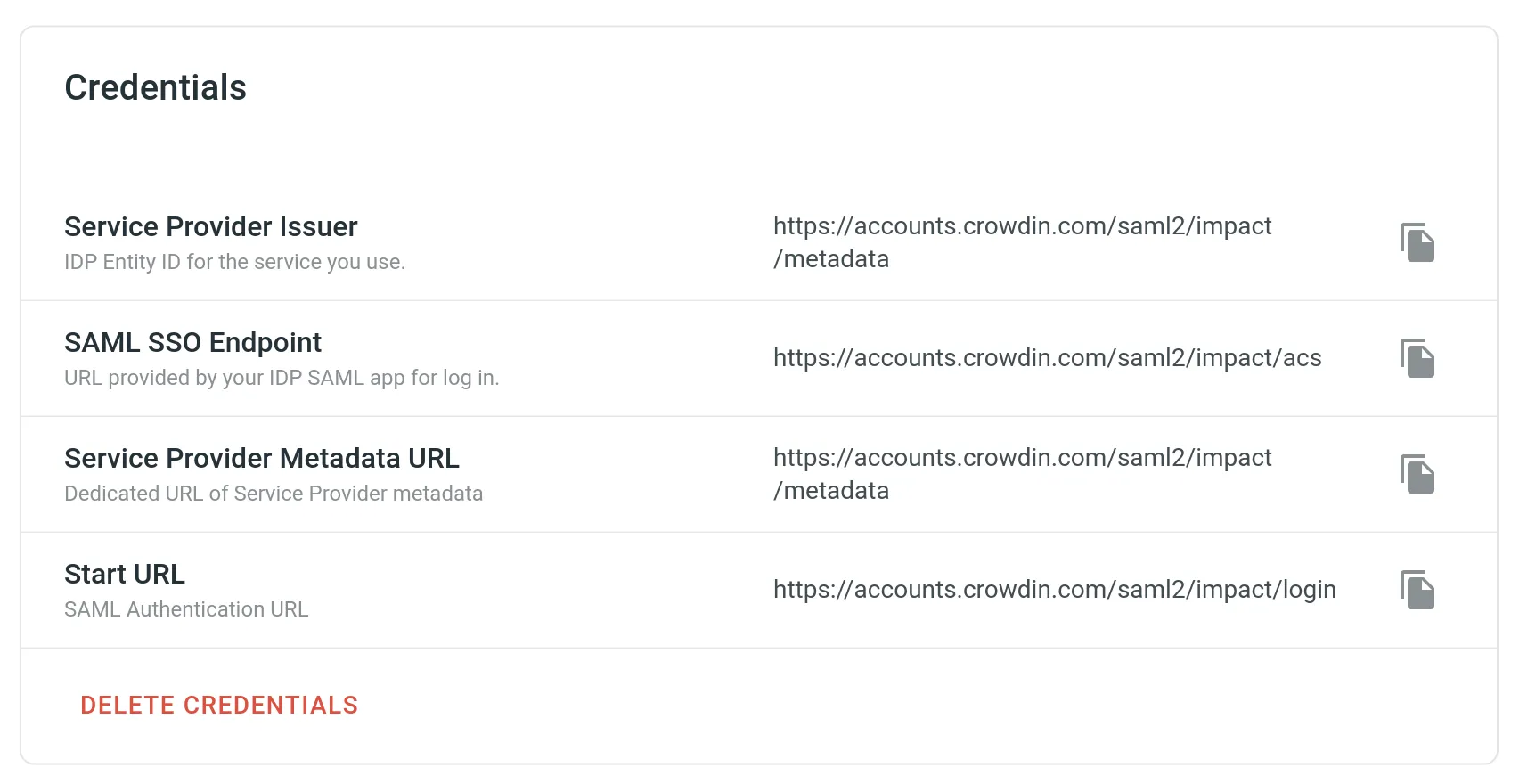
- Take the credentials from the SAML Single Sign-On page and paste them into the IDP settings.
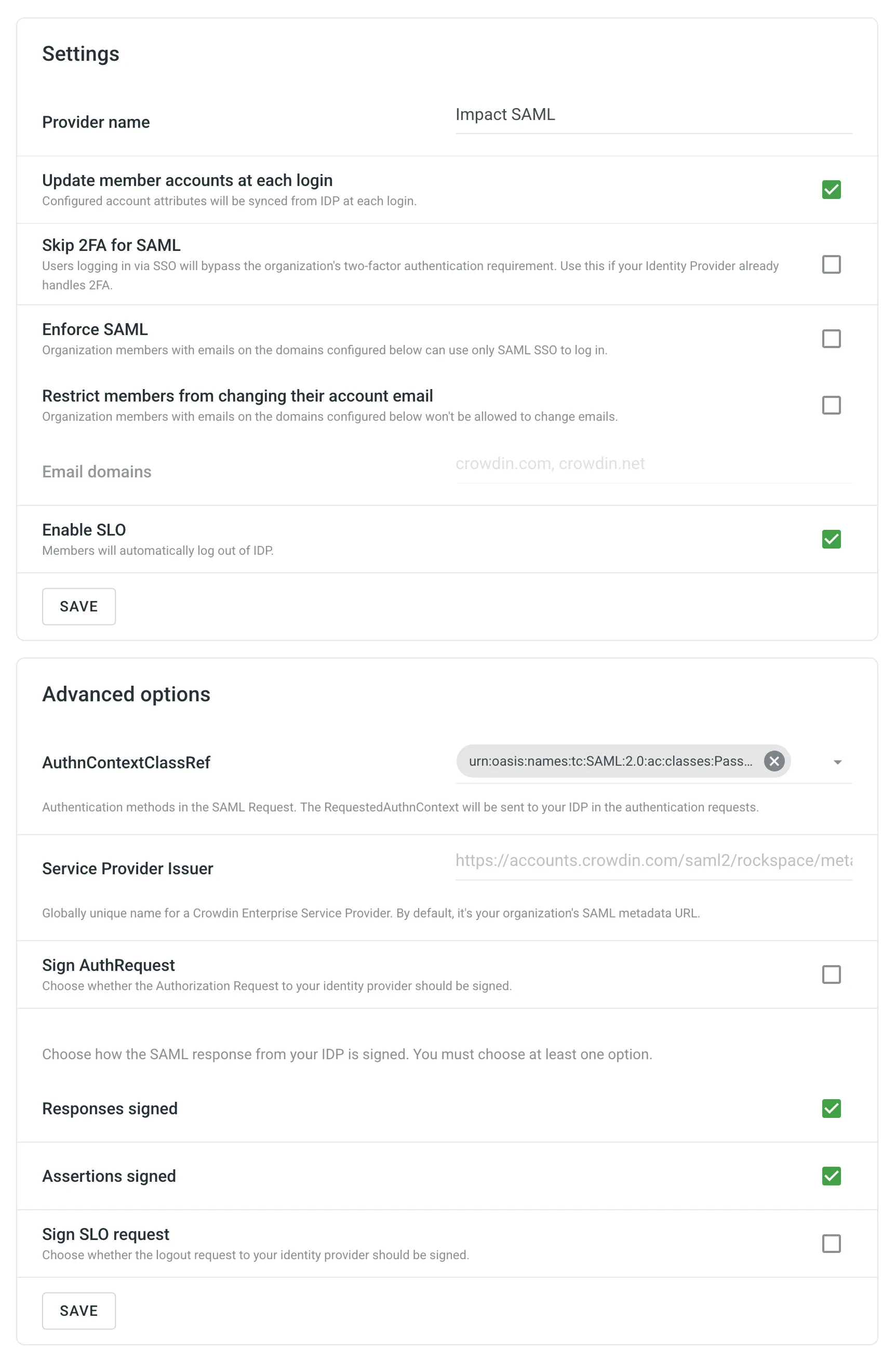
- Set the preferred configurations in the Settings and Advanced options sections depending on the configurations on the IDP side and click Save.
- Go back to the Authentication page and enable the SAML authentication method.
- As a result, on the login page, users will be able to use SAML for logging into your Crowdin Enterprise organization.
The SAML Settings section provides you with different options that let you fine-tune your SAML behavior.
- Provider name – the name of the SAML authentication method that will be displayed on your Crowdin Enterprise login page.
- Update member accounts at each login – select whether you’d like the configured account attributes to be synced from IDP at each login of the organization member. These attributes are synced from IDP during the account creation.
- Skip 2FA for SAML – select whether users logging in via SAML SSO will bypass the organization’s two-factor authentication requirement. Enable this option if your Identity Provider already handles 2FA.
- Enforce SAML – select whether organization members with emails on the domains configured in the Email domains can use only SAML SSO to log in.
- Restrict members to change their account email – select whether you’d like to restrict members to change their Crowdin Enterprise emails.
- Email domains – email domains related to organization members that use SAML SSO to log in.
- Enable SLO – select whether organization members should be logged out of IDP when logging out of your Crowdin Enterprise organization.
- AuthnContextClassRef – authentication method used in SAML request. By default, it’s authentication via username and password over a protected session.
- Service Provider Issuer – globally unique name for a Crowdin Enterprise Service Provider. By default, it’s your organization’s SAML metadata URL.
- Sign AuthRequest – select whether to sign the authorization request to your IDP.
The following options allow you to choose how the SAML response from your IDP is signed. Use at least one option.
- Responses signed - Indicates a requirement for the SAML Responses received by Crowdin Enterprise to be signed.
- Assertions signed - Indicates a requirement for the SAML Assertions received by Crowdin Enterprise to be signed.
- Sign SLO request - Indicates a requirement for the Single Logout (SLO) requests sent to your identity provider to be signed.
You can map attributes in the IDP response to user attributes used in Crowdin Enterprise. See the available attributes in the following table.
| Parameter | Details |
|---|---|
firstName | Type: stringDescription: The first name of the user stored on the IDP. |
lastName | Type: stringDescription: The last name of the user stored on the IDP. |
timeZone | Type: stringDescription: The timezone of the user. |
avatar | Type: stringDescription: The absolute URL to user’s profile picture. |
Any users already logged in after you’ve set up and enabled the SAML SSO will remain logged in. Further on, users that chose SAML as their login method will log into your Crowdin Enterprise organization with their IDP account. If there is no account for some user in your organization, an account will be created automatically during the login process into your Crowdin Enterprise organization.
To set up Crowdin Enterprise SAML SSO in your Google Workspace, follow the steps below.
- Open the Google Admin console using an administrator account.
- From the Admin console Home page, go to Apps > SAML apps.
- Click Add at the bottom right.
- Click Set up my own custom app. The Google IdP Information window opens and the SSO URL and Entity ID fields automatically populate.
- Copy the SSO URL, Entity ID, and download the certificate.
- In a separate browser tab or window, log in to your Crowdin Enterprise Organization, open the Organization Settings > Authentication page, and click on SAML at the bottom of the Authentication methods list.
- Enter the information you copied in Step 5 (paste the SSO URL in the SAML SSO Endpoint field, Entity ID in the Identity Provider Issuer field, and drag and drop your certificate file to the Public Certificate field), click Save and then return to the Google Admin console.
- Click Next.
- In the Basic information window, add an application name (for example Crowdin Enterprise) and optionally add a description.
- (Optional) Upload a PNG or GIF file to serve as an icon for your Crowdin Enterprise SSO app. The icon image should be 256 pixels square. You can find the Crowdin icon on the Using the Crowdin Logo page.
- Click Next.
- In the Service Provider Details window, you need to enter an ACS URL, Entity ID, leave the Start URL empty, leave the Signed Response box cleared, and set the Name ID Format to PERSISTENT.
- Switch to your Crowdin Enterprise Organization Settings > Authentication > SAML where all the values for Step 12 could be found.
- Copy and paste the SAML SSO Endpoint in the ACS URL field, Service Provider Issuer in the Entity ID field in your Google Admin console, clear the Responses signed option, and click Save.
- Select SAML in the Authentication methods list so that your users could use it as the desired authentication method to log in to your Crowdin Enterprise organization from the login page.
- Switch to your Google Admin console and click Next.
- Click Finish on the Attribute Mapping page.
- In the Setting up SSO for Crowdin Enterprise window, click OK.
- From the Admin console Home page, go to Apps > SAML apps.
- Select your new Crowdin Enterprise SAML app.
- At the top right of the gray box, click Edit Service .
- To turn service on or off for everyone in your organization, click On for everyone or Off for everyone, and then click Save.
- To turn service on or off only for users in an organizational unit:
- On the left, select the organizational unit.
- Select On or Off and then click Save. Read more about the organizational structure of Google Workspace.
- To turn service on for a set of users across or within organizational units, select an access group. For details, go to turn on a service for a group.
- Ensure that the email addresses your users use to log in to the SAML app match the email addresses they use to log in to your Google domain.
- Open the single sign-on URL for your new Crowdin Enterprise SAML app by clicking on the Crowdin Enterprise in the Google apps menu. Crowdin Enterprise could be found in the app list along with Google Drive, Gmail, and others. You should be automatically redirected to the Google login page.
- Enter your login credentials. After your login credentials are authenticated, you’re automatically redirected to Crowdin Enterprise.
To set up Crowdin Enterprise SAML SSO in your Microsoft Azure, follow the steps below.
Add Confluence SAML SSO by Microsoft from the Gallery
Section titled “Add Confluence SAML SSO by Microsoft from the Gallery”- Open the Azure portal using an administrator account.
- On the left navigation panel, select the Microsoft Entra ID service.
- Click on the Manage section and select Enterprise applications from the list. You’ll be redirected to Enterprise applications > All applications.
- To add a new application, click New application.
- In the Search application field, type Confluence SAML SSO by Microsoft.
- Select Confluence SAML SSO by Microsoft from the results panel and then click Create. Wait a few seconds while the app is being added.
Follow these steps to set up Microsoft Entra ID SSO in the Azure portal:
- As soon as the application is added, you’ll be redirected to its Overview page. On the Confluence SAML SSO by Microsoft application Overview page, find the Manage section and select Single sign-on.
- On the Select a single sign-on method page, select SAML.
- You are now on the Set up single sign-on with SAML page. The following configurations will be happening in the different sections of this page.
- Click on the Basic SAML Configuration section.
- Enter your Crowdin Enterprise service provider details here and click Save.
- Identifier (Entity ID):
https://accounts.crowdin.com/saml2/{your-organization-name}/metadata - Reply URL (Assertion Consumer Service URL):
https://accounts.crowdin.com/saml2/{your-organization-name}/acs - Sign on URL:
https://accounts.crowdin.com/saml2/{your-organization-name}/login
- Identifier (Entity ID):
- Click on the Attributes & Claims section.
- Click on the claim in the Required claim section.
- On the Manage claim page, select Persistent for the Name identifier format and select user.mail for the Source attribute, click Save.
- Click on the SAML Certificates section.
- Select Sign SAML response and assertion for the Signing Option and click Save.
- Click Download toward the Certificate (Base64) from the SAML Certificates section.
- Go to the Set up Confluence SAML SSO by Microsoft section.
- Copy the Login URL, Microsoft Entra Identifier, Logout URL.
- In a separate browser tab or window, log in to your Crowdin Enterprise Organization, open the Organization Settings > Authentication page, and click on SAML at the bottom of the Authentication methods list.
- Enter the information you copied in the Azure portal and click Save.
- Paste the Login URL in the SAML SSO Endpoint field.
- Paste Microsoft Entra Identifier in the Identity Provider Issuer field.
- Paste Logout URL in the SAML SLO Endpoint field.
- Drag and drop your certificate file to the Public Certificate field.
- You’ll be redirected back to the Organization Settings > Authentication page. Select the checkbox next to the SAML in the bottom of the Authentication methods list so that your users could use it as the desired authentication method to log in to your Crowdin Enterprise organization from the login page.
Depending on the authentication method you use in the Azure portal, in some cases, it might be necessary to change the default value for the AuthnContextClassRef parameter on the SAML Single Sign-On page in Crowdin Enterprise.
To allow all possible authentication methods, change AuthnContextClassRef parameter to the unspecified value.
In this section, you’ll enable users to use Azure single sign-on by granting access to your Crowdin Enterprise Organization.
- In the Azure portal, select Enterprise Applications, and then select All applications.
- In the applications list, select Confluence SAML SSO by Microsoft.
- In the app’s overview page, find the Manage section, and select Users and groups.
- Click Add user/group, then on the Add Assignment pane, click None Selected under Users and groups.
- In the Users and groups dialog, select your own account from the Users list to be able to test the SAML SSO, then click the Select button at the bottom of the screen, then click Assign. In the same way, you’ll be able to assign more users anytime.
- On the Confluence SAML SSO by Microsoft application Overview page, find the Manage section and select Single sign-on.
- Scroll down to the Test single sign-on with Confluence SAML SSO by Microsoft section and click Test.
- On the right-side pane, click Sign in as current user. After your login credentials are authenticated, you’re automatically redirected to Crowdin Enterprise.
To set up Crowdin Enterprise SAML SSO in your Okta, follow the steps below.
- Open the Okta Dashboard using an administrator account.
- From the Dashboard page, go to Applications.
- Click Add Application.
- Click Create New App.
- In the Create a New Application Integration dialog, set Platform to Web and Sign on method to SAML 2.0, click Create.
- On the Create SAML Integration page, add an application name (for example Crowdin Enterprise) on the General Settings step.
- (Optional) Upload a PNG, JPG, or GIF file to serve as a logo for your Crowdin Enterprise SSO app. The image should have dimensions less than 1400x400px and be less than 100k in size. You can find the Crowdin icon on the Using the Crowdin Logo page.
- Keep the App visibility options cleared, click Next.
- On the Configure SAML step > SAML Settings section, you need to enter Single sign on URL, Audience URI (SP Entity ID), leave the Default RelayState empty, set the Name ID Format to Persistent, Application username to Email, click Next.
Single sign on URL:
https://accounts.crowdin.com/saml2/{your-organization-name}/acs
Audience URI (SP Entity ID):https://accounts.crowdin.com/saml2/{your-organization-name}/metadata - On the Feedback step, select the This is an internal app that we have created option, click Finish.
- After you finished setting up the app on the Okta’s side, you’ll be redirected to the app’s Sign On tab. In the Settings section, click View SAML setup instructions.
- In the new browser tab, you’ll see the credentials that need to be specified in your Crowdin Enterprise Organization Settings > Authentication page > SAML.
- Copy the Identity Provider Single Sign-On URL, Identity Provider Issuer, and download the certificate.
- In a separate browser tab or window, log in to your Crowdin Enterprise Organization, open the Organization Settings > Authentication page, and click on SAML at the bottom of the Authentication methods list.
- Enter the information you copied in Step 13 (paste the Identity Provider Single Sign-On URL in the SAML SSO Endpoint field, Identity Provider Issuer in the Identity Provider Issuer field, and drag and drop your certificate file to the Public Certificate field), click Save.
- Select the checkbox next to SAML in the Authentication methods list so that your users could use it as the desired authentication method to log in to your Crowdin Enterprise organization from the login page.
In this section, you’ll enable users to use Okta single sign-on by granting access to your Crowdin Enterprise Organization.
- Open your Okta Dashboard using an administrator account and go to Applications.
- Click on your new Crowdin Enterprise SAML app.
- Switch to the Assignments tab, click Assign, and select Assign to Groups.
- In the Assign Crowdin Enterprise to Groups dialog, click Assign on Everyone to enable Crowdin Enterprise SAML app to all users in your organization, click Done. Alternatively, you can assign separate groups or individual users.
- On the Crowdin Enterprise login page, select your organization and click Log in.
- Click on SAML. You should be automatically redirected to the Okta login page.
- Enter your login credentials. After your login credentials are authenticated, you’re automatically redirected to Crowdin Enterprise.
To set up Crowdin Enterprise SAML SSO in your OneLogin, follow the steps below.
Add OneLogin SAML Test (IdP) from the App Catalog
Section titled “Add OneLogin SAML Test (IdP) from the App Catalog”- Open the OneLogin Admin Console using an administrator account.
- From the Admin Console page, go to Applications.
- To add a new application, click Add App.
- On the Find Applications page, type OneLogin SAML Test (IdP) in the search box.
- Select OneLogin SAML Test (IdP) from the search results list. Wait a few seconds while the app is being added.
- Update or rename the Display Name (for example to Crowdin Enterprise).
- (Optional) Replace default app icons with a PNG or SVG file for your Crowdin Enterprise SSO app. You can find the Crowdin icon on the Using the Crowdin Logo page, click Save.
- You are now in the Info tab. Click the Configuration tab. Enter your Crowdin Enterprise service provider details here and click Save to proceed.
SAML Consumer URL:
https://accounts.crowdin.com/saml2/{your-organization-name}/acs
SAML Audience:https://accounts.crowdin.com/saml2/{your-organization-name}/metadata
SAML Recipient:https://accounts.crowdin.com/saml2/{your-organization-name}/acs
SAML Single Logout URL:https://accounts.crowdin.com/saml2/{your-organization-name}/slo
ACS URL Validator:^https:\/\/accounts\.crowdin\.com\/saml2\/{your-organization-name}\/acs$ - Navigate to the SSO tab in OneLogin and copy the Issuer URL, SAML 2.0 Endpoint (HTTP), and X.509 Certificate. To copy the X.509 certificate, click View Details.
- In a separate browser tab or window, log in to your Crowdin Enterprise Organization, open the Organization Settings > Authentication page, at the bottom of the Authentication methods list click on SAML.
- Enter the information you copied in Step 8 (paste the Issuer URL in the Identity Provider Issuer field, SAML 2.0 Endpoint (HTTP) in the SAML SSO Endpoint field, and X.509 certificate to the Public Certificate field), click Save.
- Select the checkbox next to SAML in the Authentication methods list so that your users could use it as the desired authentication method to log in to your Crowdin Enterprise organization from the login page.
In this section, you’ll grant users access to your new Crowdin Enterprise SAML SSO app.
- Open the OneLogin Admin Console using an administrator account.
- From the Admin Console page, go to Applications.
- Click on your new Crowdin Enterprise SAML SSO app.
- Navigate to the Access tab and specify the roles that should have access to this app. If you don’t have the necessary role you can add a new role via Users > Roles specifying access to the needed apps. You can assign users to a new role via Users page.
- On the Crowdin Enterprise login page, select your organization and click Log in.
- Click on SAML. You should be automatically redirected to the OneLogin login page.
- Enter your login credentials. After your login credentials are authenticated, you’re automatically redirected to Crowdin Enterprise.
To set up Crowdin Enterprise SAML SSO in your Auth0, follow the steps below.
- Open the Auth0 Management Dashboard using an administrator account.
- From the Dashboard, go to Applications.
- Click + CREATE APPLICATION on the right.
- In the Name field, specify an application name (for example Crowdin Enterprise), select the Regular Web Applications application type, click CREATE.
- Go back to Dashboard > Applications.
- Find the row for the application you just created, and click on the Settings icon to the right of the application name.
- (Optional) Specify the URL for your Crowdin Enterprise SSO app logo in the Application Logo field. You can find the Crowdin icon on the Using the Crowdin Logo page.
- Switch to the Addons tab.
- Click on SAML2 WEB APP.
- In the appeared dialog, specify the Application Callback URL.
Application Callback URL:
https://accounts.crowdin.com/saml2/{your-organization-name}/acs - In the Settings paste the following snippet
This way the NameID would be set to the user email address.{"nameIdentifierProbes": ["http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]}
- Scroll down and click ENABLE.
- Scroll up and switch to the Usage tab.
- In the Usage tab, you’ll see the credentials that need to be specified in your Crowdin Enterprise Organization Settings > Authentication page > SAML.
- Copy the Issuer, Identity Provider Login URL, and download the certificate.
- In a separate browser tab or window, log in to your Crowdin Enterprise Organization, open the Organization Settings > Authentication page, and click on SAML at the bottom of the Authentication methods list.
- Enter the information you copied in Step 14 (paste the Issuer in the Identity Provider Issuer field, Identity Provider Login URL in the SAML SSO Endpoint field, and drag and drop your certificate file to the Public Certificate field), click Save.
- Select the checkbox next to SAML in the Authentication methods list so that your users could use it as the desired authentication method to log in to your Crowdin Enterprise organization from the login page.
Manage Access to Crowdin Enterprise SAML App
Section titled “Manage Access to Crowdin Enterprise SAML App”By default, all users associated with a single Auth0 tenant are shared between the tenant’s applications (and therefore have access to the applications). If necessary you can restrict some users’ access to the application using rules. See this rule as an example.
- On the Crowdin Enterprise login page, select your organization and click Log in.
- Click on SAML. You should be automatically redirected to the Auth0 login page.
- Enter your login credentials. After your login credentials are authenticated, you’re automatically redirected to Crowdin Enterprise.